My issue is that the archives I keep for my blog site are getting corrupted and stuff is going missing. So I am archiving using a more secure system that only works in Linux and Mac. You can't use it in Windows, but, heh, I don't care. On top of that I am running sha256sum, which is a Linux command that gives you a read out of a unique signature, so it is easy to see subsequently if someone has tampered with your archive.
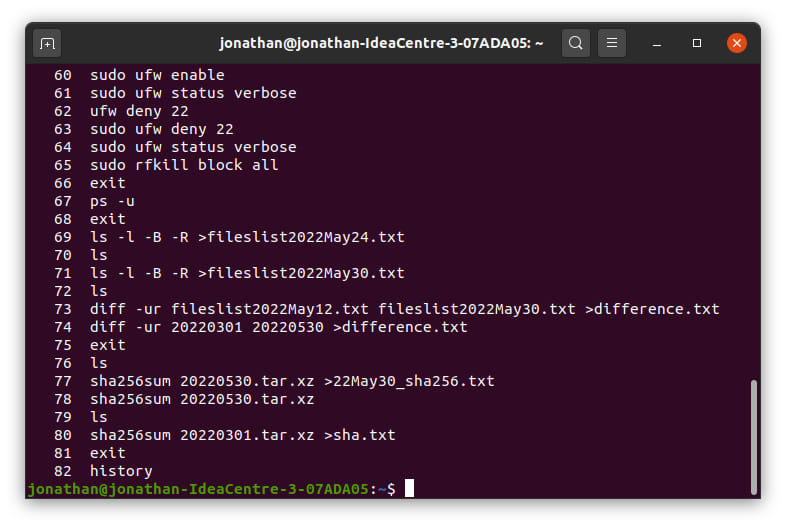
You can see the two identical commands. They are about two thirds down the list. The first produced a blank file. This is impossible. I have just run the command again (to check that I had not made some sort of mistake) and sure enough it outputted a file with the signature. Oh and by the way, a little earlier on you can see the rfkill command which should deny radio (ie wifi) access. The ufw commands are setting up the firewall. Deny 22 is to close SSH. I have a firewall even though I unplug the ethernet. This is belt, braces and a second set of belt and braces.
But the point is, this could not happen on its own. Computers are not like that. A hacker has done this on purpose.
But how?
Somebody recently gently suggested that I must be paranoid. I had to explain that if you are not paranoid, you are not paying attention.
Link to video showing the trouble I had getting this to upload.